In Brief
The SECANT platform enhances the capabilities of organisations’ stakeholders, implementing (a) collaborative threat intelligence collection, analysis and sharing; (b) innovative risk analysis specifically designed for interconnected nodes of an industrial ecosystem; (c) cutting-edge trust and accountability mechanisms for data protection and (d) security awareness training for more informed security choices. The proposed solution’s effectiveness and versatility will be validated in four realistic pilot use case scenarios applied in the healthcare ecosystem. Ultimately, SECANT contributes decisively towards improving the readiness and resilience of the organisations against the crippling modern cyber-threats, increasing the privacy, data protection and accountability across the entire interconnected ICT ecosystem, and reducing the costs for security training in the European market.
Project Information
H2020-EU.3.7.4., H2020-EU.3.7.
Funded Under
101019645
Grant agreement ID
NTT Data Spain SLU
Coordinated by
1 September 2021
Start date
31 August 2024
End date
€ 6.567.958,75
Overall budget
Objectives
Objective #1
To identify the user, technical and business requirements and design the architecture of a dynamic and highly flexible risk assessment platform for organizations.
Objective #2
To design and implement a dynamic, evidence-based, sophisticated security and privacy risk assessment framework that can deal with the cascading effects of cyber-attacks and with propagated vulnerabilities in interconnected complex ICT systems, services, and applications.
Objective #3
To design and implement a collaborative toolkit that allows the organization stakeholders and European CERTs/CSIRTs create and exchange dynamic vulnerability databases, as well as taxonomies for cyber-attacks targeting ICT systems, technologies, applications and services.
Objective #4
To design and implement a tailored data protection and multi-level accountability framework, relying on a distributed ledger system, that can establish trust, integrity and protect sensitive data.
Objective #5
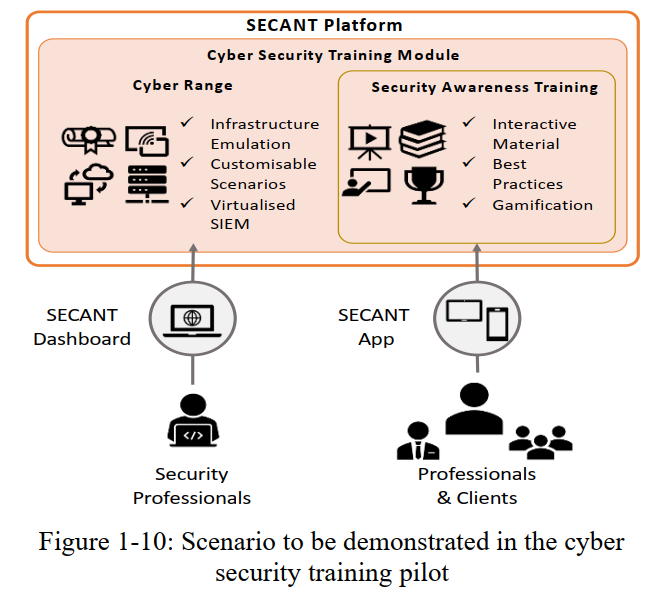
To design and develop user interfacing applications and security training platforms with cyber range capabilities that can enable all stakeholders of the organizations’ ecosystem to make smarter security decisions with training and simulated social engineering.
Objective #6
To demonstrate and validate the integrated SECANT Platform across four realistic pilot demonstrators.
Objective #7
To ensure wide communication and scientific dissemination of the SECANT results to the research, academic, and professional community, efficient exploitation and business planning of the SECANT concepts and solutions to the market, and contribution of specific project results to relevant standardization bodies.





















Challenge #1
New models of remote delivery, especially in complex ICT infrastructures such as healthcare, increase the potential impact of cyber security breaches to a level that has not been experienced before. Compromising the confidentiality, integrity or availability of the information exchanged, to implement platforms that permit people to work from home, means that attack surface is considerably broadened and adversaries can disclose sensitive information, affect the integrity or correctness of the transmitted data, or even stop processes and services from taking place.

Challenge #2
Modern ICT systems rely heavily on Internet of Things devices which act as sensors, used for monitoring and diagnostics. Wearable devices are also very popular as they offer convenience through their smaller factor and a wide range of services constantly expanding. As they are connected to networks, wearables are also used to monitor the health of patients through their integrated sensors. The exceptionally large volumes of data generated by IoT devices are impractical to monitor continuously for signs of compromise

Challenge #3
A lot of organizations and especially those relying on complex ICT infrastructures are often regarded as poor in terms of their cyber security practices because people processing private and sensitive data, fall victims of malicious parties, exposing entry points to ICT infrastructures well protected from outsiders. The level of security awareness is still disproportionately low compared to the criticality and potential of a security breach in critical sectors.
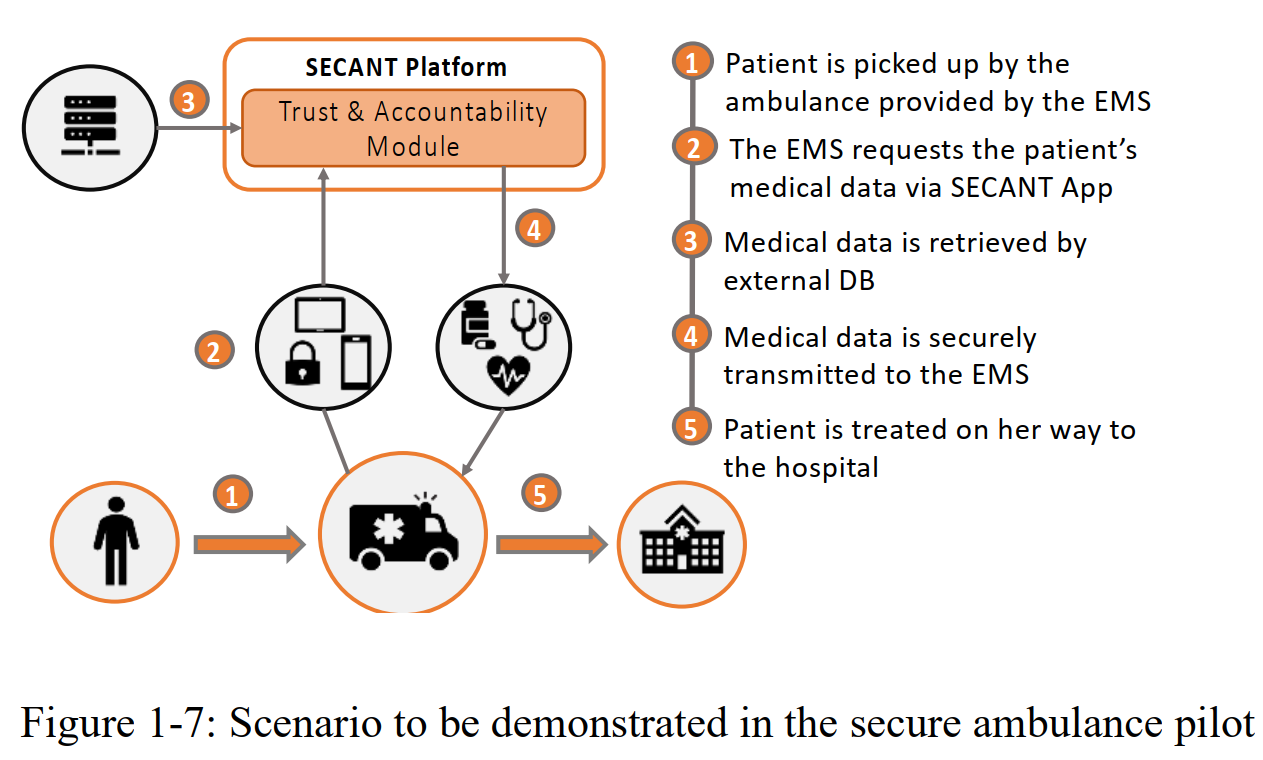
Use Case #1: Protecting the connected ambulance of the future
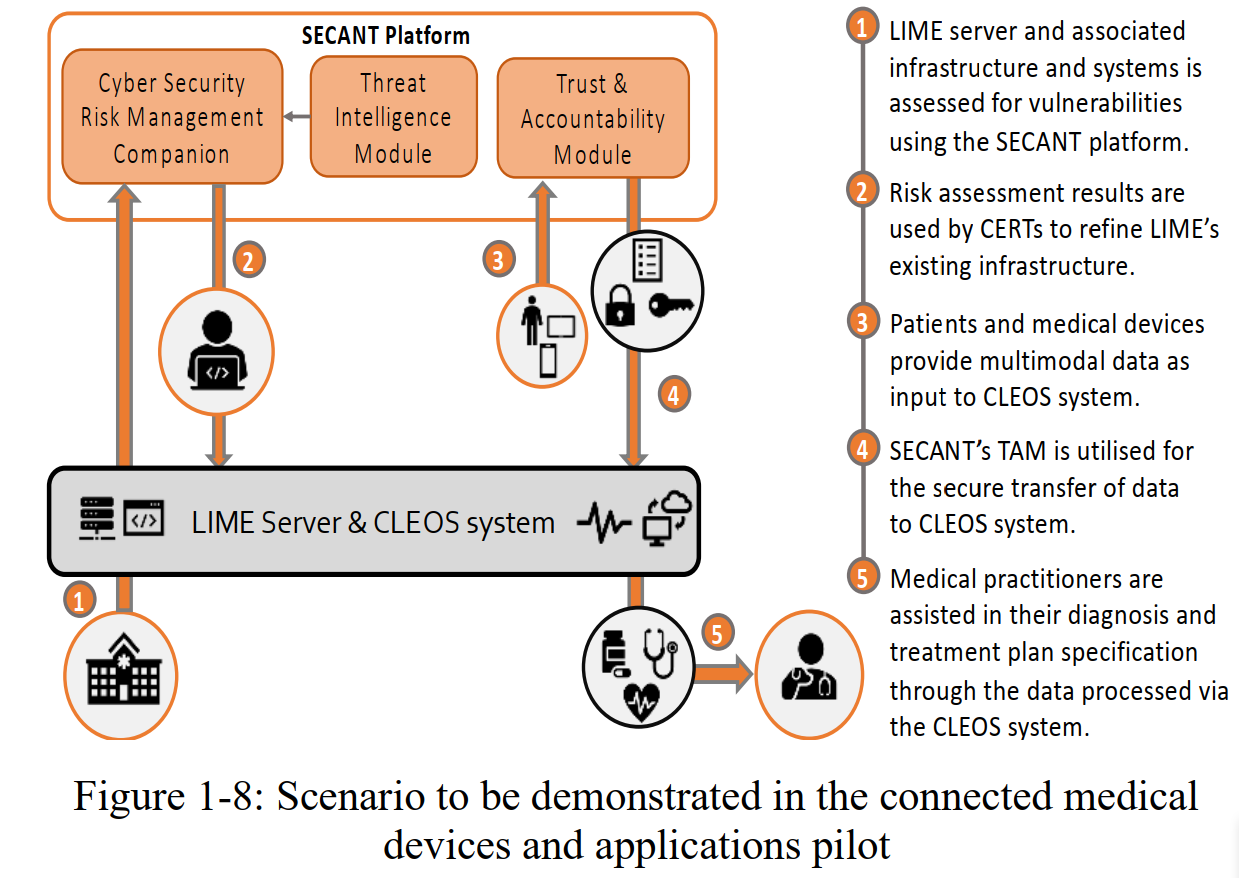
Use Case #2: Cyber security for connected medical devices and mobile applications

Use Case #3: Health data protection in the healthcare supply chain